Azure VM (Virtual Machines) Basic Training¶
The below is a program of exercises to understand how to deploy and run a public cloud workload securely.
1. Basic Deployment¶
Microsoft Documentation - Main Documentation for learning more about Azure VMs
1.1. Prerequisites¶
1.2. Portal Deployment¶
- Microsoft Portal Exercise - Default exercise for deploying VMs via Portal
1.3. Sign in to Azure¶
Sign in to the Azure portal.
1.4. Create virtual machine¶
- Enter virtual machines in the search.
- Under Services, select Virtual machines.
- In the Virtual machines page, select Create and then Virtual machine. The Create a virtual machine page opens.
- In the Basics tab, under Project details, make sure the correct subscription is selected and then choose to Create new resource group. Enter myResourceGroup for the name.*. Image TODO
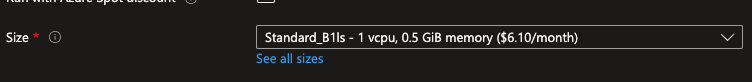
- Under Instance details, enter myVM-name for the Virtual machine name, and choose Standard_B1ls for your Image. Size availability and pricing are dependent on your region and subscription. Leave the other defaults.
 > NOTE: Some users will now see the option to create VMs in multiple zones. To learn more about this new capability, see Create virtual machines in an availability zone
> NOTE: Some users will now see the option to create VMs in multiple zones. To learn more about this new capability, see Create virtual machines in an availability zone - Under Administrator account, select SSH public key.
- In Username enter azureuser.
- For SSH public key source, leave the default of Generate new key pair, and then enter myKey for the Key pair name. > Image TODO
- Under Inbound port rules > Public inbound ports, choose Allow selected ports and then select SSH (22) and HTTP (80) from the drop-down. > Image TODO
- Leave the remaining defaults and then select the Review + create button at the bottom of the page.
- On the Create a virtual machine page, you can see the details about the VM you are about to create. When you are ready, select Create.
- When the Generate new key pair window opens, select Download private key and create resource. Your key file will be download as myKey.pem. Make sure you know where the
.pemfile was downloaded; you will need the path to it in the next step. - In Disks section, under Disk options, create new virtual network as name-vnet.
- Confirm that Delete public IP and NIC when VM is deleted is selected.
- In Management section, under Monitoring, select disable.
- Click Review + Create in the buttom left hand corner, to finalise the creation of the VM. Allow for the validation to complete and click on create.
- Download the created private key and create resource.
- When the deployment is finished, select Go to resource.
- On the page for your new VM, select the public IP address and copy it to your clipboard. > Image TODO
2. Connect to virtual machine¶
Create an SSH connection with the VM.
Linux:
- If you are on a Mac or Linux machine, open a Bash prompt and set read-only permission on the .pem file using
chmod 400 ~/Downloads/myKey.pem. If you are on a Windows machine, open a PowerShell prompt.
Linux and Windows:
- At your prompt, open an SSH connection to your virtual machine. Replace the IP address with the one from your VM, and replace the path to the
.pemwith the path to where the key file was downloaded.
TIP: The SSH key you created can be used the next time your create a VM in Azure. Just select the Use a key stored in Azure for SSH public key source the next time you create a VM. You already have the private key on your computer, so you won't need to download anything.
2.1. Install Docker¶
Docker is an open source containerization platform. It enables developers to package applications into containers—standardized executable components combining application source code with the operating system (OS) libraries and dependencies required to run that code in any environment. Containers simplify delivery of distributed applications, and have become increasingly popular as organizations shift to cloud-native development and hybrid multicloud environments.
Further information reagrding docker
2.2. Install Web Application¶
Caddy simplifies your infrastructure. It takes care of TLS certificate renewals, OCSP stapling, static file serving, reverse proxying, Kubernetes ingress, and more.
Further information reagrding caddy
3. Security Hardening¶
3.1. Basic¶
Basic security hardening is accepatable for testing but is not recommended alone for extensive development and production workloads
3.1.1. Network Security Group (NSG)¶
- Whitelist/Allow IP
> Make a note of the IP address you are currently utilsing
- In the VM portal, select networking in the setting blade.
- Select Inbound port rules, select the SSH rule to edit the rule setting.
- Change source from Any to IP Addresses.
- In Source IP addresses/CIDR ranges add the IP address previously noted.
- Click Save
- Repeat steps for HTTP (port 80)
- NSG Logging (Sentinel)
- Sign in to the portal.
- Select All services, then type network security groups. When Network security groups appear in the search results, select it.
- Select the NSG you want to enable logging for.
- Under MONITORING, select Diagnostics logs, and then select Turn on diagnostics, as shown in the following picture: > Image TODO
- Under Diagnostics settings, enter, or select the following information, and then select Save: | Setting | Value | | ------------------------------------------------------------------------------------------- | -------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- | | Name | A name of your choosing. For example: myNsgDiagnostics | | Archive to a storage account, Stream to an event hub, and Send to Log Analytics | You can select as many destinations as you choose. To learn more about each, see Log destinations. | | LOG | Select either, or both log categories. To learn more about the data logged for each category, see Log categories. |
- View and analyze logs. For more information, see Query logs in Microsoft Sentinel.
3.2. Moderate¶
3.2.1. Web Application Firewall (WAF)¶
- Create an application gateway
- Select Create a resource on the left menu of the Azure portal. The New window appears.
- Select Networking and then select Application Gateway in the Featured list.
- Basics tab
- On the Basics tab, enter these values for the following application gateway settings:
- Resource group: Select myResourceGroupAG for the resource group. If it doesn't exist, select Create new to create it.
- Application gateway name: Enter name_WAF for the name of the application gateway.
- Tier: select WAF V2.
- Region: select Australia East
- Enable autoscaling: select No
- HHTP2: seclect Disabled
- WAF Policy: Select Create new, type a name for the new policy name_waf_policy, tick Add bot Portection and then select OK. This creates a basic WAF policy with a managed Core Rule Set (CRS).
- For Azure to communicate between the resources that you create, it needs a virtual network. You can either create a new virtual network or use an existing one. In this example, you'll create a new virtual network at the same time that you create the application gateway. Application Gateway instances are created in separate subnets. You create two subnets in this example: one for the application gateway, and another for the backend servers.
- Under Configure virtual network, select the the exisitng VM vnet name-vnet:
- Subnet name (Create Application Gateway subnet for VM): Click Manage Subnet Configuration.
The application gateway subnet can contain only application gateways. No other resources are allowed. - In VM subnets, click + Subnets.
- In Add Subnet, add a name *anme_WAF to the new subnet. Use the Default Subnet address Range and Click save
- Back in Create application Gateway pane, select newly create subnet. > Image TODO
- On the Basics tab, accept the default values for the other settings and then select Next: Frontends.
- On the Basics tab, enter these values for the following application gateway settings:
- Frontends tab
- On the Frontends tab, verify Frontend IP address type is set to Public.
You can configure the Frontend IP to be Public or Private as per your use case. In this example, you'll choose a Public Frontend IP. > NOTE: For the Application Gateway v2 SKU, there must be a Public frontend IP configuration. You can still have both a Public and a Private frontend IP configuration, but Private only frontend IP configuration (Only ILB mode) is currently not enabled for the v2 SKU. - Select Add new for the Public IP address and enter name_waf_public_ip for the public IP address name, and then select OK.
- Select Next: Backends.
- On the Frontends tab, verify Frontend IP address type is set to Public.
- Backends tab
> The backend pool is used to route requests to the backend servers that serve the request. Backend pools can be composed of NICs, virtual machine scale sets, public IP addresses, internal IP addresses, fully qualified domain names (FQDN), and multi-tenant back-ends like Azure App Service. In this example, you'll create an empty backend pool with your application gateway and then add backend targets to the backend pool.
- On the Backends tab, select Add a backend pool.
- In the Add a backend pool window that opens, enter the following values to create an empty backend pool:
- Name: Enter name_waf_backend for the name of the backend pool.
- Add backend pool without targets: Select No.
- Under Target Type select Virtual MAchine.
- Select current VM as Target
- In the Add a backend pool window, select Add.
- On the Backends tab, select Next: Configuration.
- Configuration tab
> On the Configuration tab, you'll connect the frontend and backend pool you created using a routing rule.
- Select Add a routing rule in the Routing rules column.
- In the Add a routing rule window that opens, enter name_WAF_rule for the Rule name. Add priority of 300.
- A routing rule requires a listener. On the Listener tab within the Add a routing rule window, enter the following values for the listener:
- Listener name: Enter name_WAF_rule_Listener for the name of the listener.
- Frontend IP: Select Public to choose the public IP you created for the frontend. > Accept the default values for the other settings on the Listener tab, then select the Backend targets tab to configure the rest of the routing rule.
- On the Backend targets tab, select myBackendPool for the Backend target.
- For the HTTP setting, select Add new to add a new HTTP setting. The HTTP setting will determine the behavior of the routing rule. In the Add an HTTP setting window that opens, enter nameHTTPSetting for the HTTP setting name and 80 for the Backend port. Accept the default values for the other settings in the Add an HTTP setting window, then select Add to return to the Add a routing rule window.
- On the Add a routing rule window, select Add to save the routing rule and return to the Configuration tab.
- Select Next: Tags and then Next: Review + create.
- Review + create tab > Review the settings on the Review + create tab, and then select Create to create the virtual network, the public IP address, and the application gateway. It may take several minutes for Azure to create the application gateway. Wait until the deployment finishes successfully before moving on to the next section. > Creation of the WAF can take up to 5 -30 minutes to complete
3.2.2. Configure Firewall¶
- In the newly created WAF, under settings, seclect Web Application Firewall.
- Under Configure:
- Change Tier to WAF v2
- Change WAF Status to enabled
- WAF Mode to Prevention
- Under Global Parameters, turn Inspect Request Body to off
- Under Rules:
- Change Rule Set to OWASP 3.2
- Click Save to commit changes to WAF.
3.2.3. Ingest WAF Logs to Sentinel¶
- Select Diagnostic logs.
- Select + Add diagnostic setting.
- In the Diagnostic setting blade:
- Type a Name.
- Select Send to Log Analytics.
- Choose the log destination workspace.
- Select the categories that you want to analyze (recommended: ApplicationGatewayAccessLog, ApplicationGatewayFirewallLog, FrontdoorAccessLog, FrontdoorWebApplicationFirewallLog, WebApplicationFirewallLogs).
- Click Save.
3.3. Just In Time Access (JIT)¶
You can enable JIT on a VM from the Azure virtual machines pages of the Azure portal.
TIP: If a VM already has just-in-time enabled, when you go to its configuration page you'll see that just-in-time is enabled and you can use the link to open the just-in-time VM access page in Defender for Cloud, and view and change the settings.
- From the Azure portal, search for and select Virtual machines.
- Select the virtual machine you want to protect with JIT.
- In the menu, select Configuration.
- Under Just-in-time access, select Enable just-in-time.
> This enables just-in-time access for the VM using the following default settings:
- Windows machines:
- RDP port 3389
- Three hours of maximum allowed access
- Allowed source IP addresses is set to Any
- Linux machines:
- SSH port 22
- Three hours of maximum allowed access
- Allowed source IP addresses is set to Any
- Windows machines:
- To edit any of these values, or add more ports to your JIT configuration, use Microsoft Defender for Cloud's just-in-time page:
- From Defender for Cloud's menu, select Just-in-time VM access.
- From the Configured tab, right-click on the VM to which you want to add a port, and select edit. > Image TODO
- Under JIT VM access configuration, you can either edit the existing settings of an already protected port or add a new custom port.
- When you've finished editing the ports, select Save.
Further documentation on Just In Time Access
4. Advanced¶
4.1. Network Watcher¶
4.1.1. Create a Network Watcher in the portal¶
Navigate to All Services > Networking > Network Watcher. You can select all the subscriptions you want to enable Network Watcher for. This action creates a Network Watcher in every region that is available.
Image TODO
When you enable Network Watcher using the portal, the name of the Network Watcher instance is automatically set to NetworkWatcher_region_name where region_name corresponds to the Azure region where the instance is enabled. For example, a Network Watcher enabled in the West Central US region is named NetworkWatcher_westcentralus.
The Network Watcher instance is automatically created in a resource group named NetworkWatcherRG. The resource group is created if it does not already exist.
If you wish to customize the name of a Network Watcher instance and the resource group it's placed into, you can use PowerShell, the Azure CLI, the REST API, or ARMClient methods described in the sections that follow. In each option, the resource group must exist before you create a Network Watcher in it.
4.2. Firewall¶
Deploy the firewall into the VNet.
-
On the Azure portal menu or from the Home page, select Create a resource.
-
Type firewall in the search box and press Enter.
-
Select Firewall and then select Create.
-
On the Create a Firewall page, use the following table to configure the firewall:
Setting Value Subscription \ Resource group Test-FW-RG Name Test-FW01 Region Select the same location that you used previously Firewall tier Standard Firewall management Use Firewall rules (classic) to manage this firewall Choose a virtual network Use existing: Test-FW-VN Public IP address Add new
Name: fw-pip -
Accept the other default values, then select Review + create.
-
Review the summary, and then select Create to create the firewall.
This will take a few minutes to deploy.
-
After deployment completes, go to the Test-FW-RG resource group, and select the Test-FW01 firewall.
-
Note the firewall private and public IP addresses. You'll use these addresses later.
4.3. DDOS Protection¶
4.3.1. Create a DDoS protection plan¶
-
Select Create a resource in the upper left corner of the Azure portal.
-
Search the term DDoS. When DDoS protection plan appears in the search results, select it.
-
Select Create.
-
Enter or select the following values.
Setting Value Subscription Select your subscription. Resource group Enter exisitng MyResourceGroup. Name Enter MyDdosProtectionPlan. Region Enter Australia East. -
Select Review + create then Create
4.3.2. Enable DDoS protection for an existing virtual network¶
- Create a DDoS protection plan by completing the steps in Create a DDoS protection plan, if you don't have an existing DDoS protection plan.
- Enter the name of the virtual network that you want to enable DDoS Protection Standard for in the Search resources, services, and docs box at the top of the Azure portal. When the name of the virtual network appears in the search results, select it.
- Select DDoS protection, under Settings.
- Select Enable. Under DDoS protection plan, select an existing DDoS protection plan, or the plan you created in step 1, and then click Save. The plan you select can be in the same, or different subscription than the virtual network, but both subscriptions must be associated to the same Azure Active Directory tenant.