Network Management Guideline¶
This guideline is a pragmatic target for an entity's network architecture to enable effective and secure network management while minimising complexity. This guide is structured around the use cases for a complex network with a design that can be adopted in stages that is highly aligned with the ACSC Network gateway hardening guidance package.
Quick network security (Zero Trust / ZTNA) for Microsoft 365 customers
Rapidly implement identify, detect and some protect controls with minimal user facing / network hardware changes:
- Implement Defender for Identity to monitor identities, DNS, Kerberos and LDAP traffic
- Turn on network protection to monitor endpoint traffic and enable UEBA
- Implement Per-app Access for user access to corporate resources (including on-prem servers and DCs) to monitor application traffic
The below steps can take months to years, but won't impede the risk reduction from the above quick steps:
- Implement webauthn (passkeys/fido) with centrally logged CIAM for all internet exposed (i.e. citizen facing) systems
- Deny direct network access to applications and iteratively improve network topology
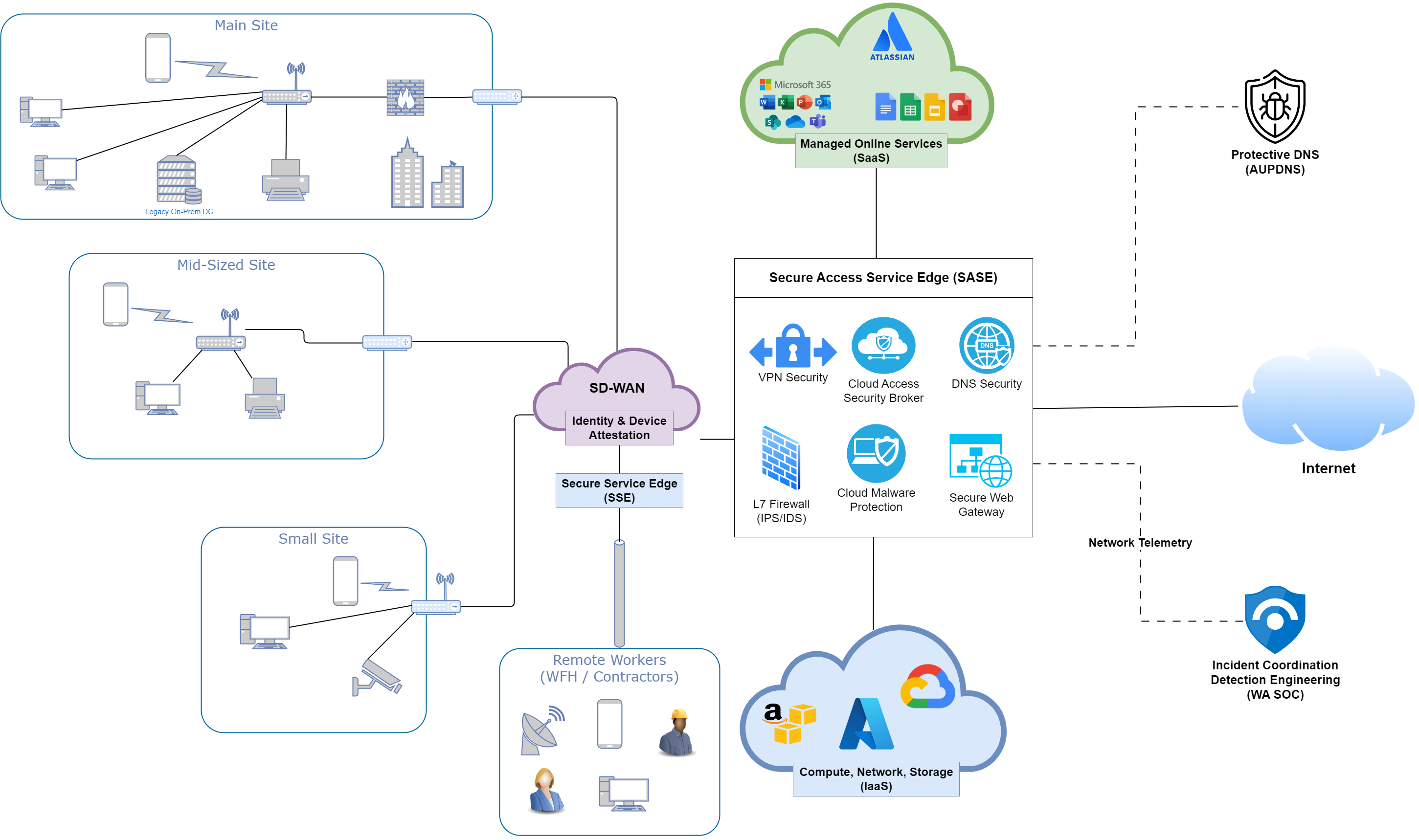
Contemporary Network Architecture¶
Organisations should strive to reduce network complexity and focus on the key outcome of connecting staff to systems securely. They should mitigate risks as much as possible by favouring managed cloud services with segregated control planes (as opposed to local direct management and the associated privileged access / shared credential complexity) and steering clear of legacy technologies such as direct Layer 3 network access.
Remote Access for staff and vendors¶
It's strongly recommended to transition from traditional VPNs to modern Secure Service Edge (SSE) platforms, that can also improve the application of network policies across an organisation. SSE and SASE platforms are available from:
- Infrastructure providers (Microsoft Security Service Edge, VMWare SASE)
- Network hardware vendors (Check Point Harmony Connect, Cisco Secure Access, FortiSASE, Palo Alto Prisma SASE)
- Virtual network vendors (Claroty SRA, Teleport (open-source with self-hosted capability), Netskope SASE, Zscaler SASE, knocknoc.io (convenient for legacy systems with not many users))
These platforms all incorporate zero trust and policy-based access logging and management out of the box and are strongly recommended for where direct network access to legacy systems is still required. All vendors, contractors and identities external to an organisation should have access controlled via such a platform to avoid third party persistent remote access (e.g. TeamViewer, LogMeIn, AnyDesk) being utilised that may not adhere to an organisations Identity and Access Management policies and procedures.
SANS ICS has a good video on secure approaches for accessing highly privileged ICS/OT environments below:
Observability & Manageability¶
Network security and management becomes much more effective once administrators have visibility over useful logs (baseline network activity, app & user identification, DNS, NetFlow data, firewall logs, HTTP/HTTPS sessions, etc). Having the ability to tie logs to specific apps and users both improves network segmentation capabilities and quality of log data for investigation and observation purposes. Most telco's have effective SD-WAN management capabilities ( Aussie Broadband, Optus, Telstra, TPG, Vocus ), while still allowing an organisation read-only access for capacity and security management functions. Organisations with the requirement and capability to manage network equipment should look towards using modern hardware with a secure cloud control plane ( Cisco DNA Center (including meraki), Forticloud ) that enable simple device management and telemetry access for all gateways, routers, switches and access points.
Web Application Firewalls (WAFs) and Content Delivery Networks (CDNs)¶
In addition to standard IP session telemetry, systems and APIs exposed to the internet that aren't protected by an SSE/SASE platform as described above should have a caching CDN and fully blocking WAF deployed between them and the internet to protect from Web Application Abuse (ACSC). Deploying and implementing a cloud based CDN and WAF such as Akamai, Amazon CloudFront, Azure Front Door, Cloudflare, F5XC, Fastly or Imperva in front of all internet exposed services is strongly recommended, as they avoid the significant risk of exposing any self-managed infrastructure directly to the internet. All of the products listed have significant detection capabilities that can also be integrated with an organisations SIEM for visibility by security operations teams.
Route Origin Authorisations (ROA) and Resource Public Key Infrastructure (RPKI)¶
As per the ACSC Gateway Security Guidance Package: Gateway Operations and Management Organisations should periodically audit their Internet number (ASN) resource assets running Border Gateway Protocol (BGP) by validating RPKI and ROA are established with Internet Service Providers (ISPs) and internet router management teams.
Adverse Event Analysis and Asset Inventory¶
Maintaining an up to date asset inventory and monitoring baseline activity enable network anomaly detection. Most if not all the products mentioned in this guideline have some capability for continuous threat detection and monitoring, real-time detection and response, or at the very least log forwarding options that can allow you SIEM to ingest data and perform alerting based on SIEM rules. The below tools notably provide tunable detection analytics linked into basic case management for security operations.
| Vendor | Network Analytics | Detection & Response | Asset Inventory |
|---|---|---|---|
| Cisco | Secure Network Analytics | Cisco XDR | Cisco Cyber Vision |
| Palo Alto | Prisma Cloud | Cortex XDR | IoT Security |
| Check Point | CloudGuard | Horizon NDR | Claroty xDome |
| Fortinet | FortiAnalyzer | FortiNDR | Claroty xDome |
Segmentation¶
Modern network segmentation helps prevent lateral movement of adversaries in an organisation and allows effective isolation/containment when responding to breaches. Through good use of network segmentation agencies can prevent certain devices or groups of devices from ever communicating with each other to adhere with principles of least privilege and protect critical infrastructure or sensitive systems. Modern SSE technologies such as those mentioned above can implement tag-based network segmentation across a broad enterprise SD-WAN including public cloud assets with appropriate egress flow monitoring. Additionally the ongoing traffic analytics from central control planes enable rapid analysis and understanding of common network flows, to simplify ongoing firewall policy management and security improvements.
Response actions may also require rapid isolation of sections of the network - a separate secure control plane (as is standard with SD-WAN and SASE architectures) with the ability to rapidly enact policy, physical and logical management boundaries between networks makes this much simpler to implement rapidly when required.
Operational Technology¶
Entities with business critical OT/ICS/SCADA assets should run a distinct operational network with associated specialist resources, that ensures encryption over all backhaul links and full segmentation from "untrusted" user networks. The cost of edge routers with full encrypted transit and management capabilities has fallen significantly, see Cisco Extended Enterprise SD-WAN with IR1101 Solution Overview for an example approach with modern cloud managed hardware.
Common Network Use Cases¶
- End Users working flexibly (baseline) - includes users at home/work/offsite accessing resources over the internet
- Collaborative technologies (Email, Telephony, Video Conferencing, Filesharing)
- Local access to office resources
- Remote access to business systems that don't support modern access protocols
- Remote access to servers (compute & storage) resources
- Operational Technology (OT) networks - all network connected devices without endpoint agents
- Industrial Control Systems
- Building Management Systems
- Sector specific technology (Critical Infrastructure & Health)
- Physical security systems (CCTV, Access Systems)
- Remote access to Operational Technology devices