Baseline for Detection Coverage (MITRE ATT&CK)¶
This document and associated checklist is intended to be used as a high-level self assessment against an organisations telemetry collection and detection analytics aligned to the MITRE ATT&CK Framework.
1. Shared Responsibility Model¶
For service providers see Supply Chain Risk Management(vendors should report detection coverage monthly and incidents within 24 hours). Otherwise ensure the Security Operations team is resourced to collect the below telemetry and manage detection, triage and response activities over them based on the organisations risk profile.
2. Data Sources¶
Below are the highest priority MITRE Data Sources to ensure telemetry and analytics are available for:
- DS0002 User Account - A profile representing a user, device, service, or application used to authenticate and access resources
- DS0025 Cloud Service - Infrastructure, platforms, or software that are hosted on-premise or by third-party providers, made available to users through network connections and/or APIs
- DS0009 Process - Instances of computer programs that are being executed by at least one thread. Processes have memory space for process executables, loaded modules (DLLs or shared libraries), and allocated memory regions containing everything from user input to application-specific data structures
- DS0017 Command - A directive given to a computer program, acting as an interpreter of some kind, in order to perform a specific task
- DS0022 File - A computer resource object, managed by the I/O system, for storing data (such as images, text, videos, computer programs, or any wide variety of other media).
- DS0029 Network Traffic - Data transmitted across a network (ex: Web, DNS, Mail, File, etc.), that is either summarized (ex: Netflow) and/or captured as raw data in an analyzable format (ex: PCAP)
- DS0015 Application Log - Events collected by third-party services such as mail servers, web applications, or other appliances (not by the native OS or platform)
2.1 Telemetry Sensors¶
Based on these data sources telemetry sensor deployment can be prioritised as follows:
- Endpoints and Servers via XDR platforms
- Network via network analytics platforms
- Public / Private cloud via API or native platforms
2.2 XDR (Detection and Response) platforms¶
XDR platforms are regularly evaluated by MITRE Engenuity (ref: Turla (2023)). Please carefully consider Supply Chain Risk when selecting such platforms - constrain to independently assessed platforms hosted in Australia, such as Microsoft Defender XDR or Trend Vision One.

Self managed platforms like Wazuh (a SIEM platform that also inventories vulnerabilities, measures CIS Benchmarks and NIST 800-53 Compliance) are effective for internally capable teams or training purposes (below excellent vid by John Hammond):
3. Detection Assets¶
The below is a high level summary of assets and services from where security logs should typically be collected. Subsequent detection queries will refer to these assets.
- Users - Identity Services (On Premise and SaaS), Application access
- Mailboxes - Email mailboxes and associated inbound/outbound flows
- Endpoints - Devices that users utilise to access organisational resources
- Servers - Hypervisors, Servers, Container Platforms
- Network Firewalls (Firewalls) - Network egress and internal network control points
- Web Application Firewalls (WAFs) - Network ingress control points
- Applications and Databases - Application logs and query logs from application runtimes (e.g. stack traces) and databases
4. Detection Checklist¶
The below checklist should be undertaken by the organisations security team to calculate the percentage coverage of assets (e.g. 8 / 10 Endpoints == 80% coverage) for a given log retention window (normally 12 months). This data is heavily used for threat hunting activities.
4.1. Excellent return on investment¶
These are available as out of the box integrations on fully SaaS platforms such as Microsoft Sentinel connected to Microsoft 365 Defender via Microsoft XDR. On-Prem sign-ins depending on the Defender for Identity require sensor deployment on all Domain Controllers (minimum version Windows Server 2012).
- Users - Query a
IPv4Address,IPv6Address,ProtocolorUser-Agent (HTTPRequestExt)across all Network Traffic for HTTPS sign ins. - Users - Query a
IPv4Address,IPv6AddressorProtocolacross all Network Traffic for On-Prem sign ins.- E.g. Defender for Identity.
- Mailboxes - Email events and URL / attachment analysis using mail server Application Logs.
- E.g. Defender for Office 365
- Query a
DomainNameorEmailAddressacross all emails. - Query a
Subject (EmailMessage)across all emails. - Query a
DomainNameorURLacross all links inside emails. - Query a
SHA256 Hash (File)across all attachments inside emails.
4.2. Very high return on investment¶
These are available as integrations with some deployment requirements on Windows, macOs and Linux endpoints using Microsoft Defender for Endpoint.
- Endpoints - Query a
IPv4Address,IPv6Address,DomainNameorURLacross all outbound Network Traffic. - Endpoints - Query a
SHA256 Hash (File),Name (File)orFileOriginUrl (File)across all Files, Processes and Commands.
4.3. High return on investment¶
Agent based network protection is relatively straightforward to ingest from application servers. High volume network traffic should be reviewed prior to ingestion to understand the volume of events and to avoid loading large quantities of low value events (such as Content Delivery Networks / File Sharing / Media Streaming logs).
- Query an
IPv4Address,IPv6AddressorDomainNameacross all inbound/outbound Network Traffic.- Servers - e.g. Defender Network Protection
- Firewalls - e.g. Sentinel 3rd party connectors
- WAFs - Query a
IPv4Address,IPv6Address,URLorUser-Agent (HTTPRequestExt)across all inbound Network Traffic.
5. Detection Analytics¶
The security tools collecting telemetry should be capable of running both built-in and custom analytics on a regular basis. Some repositories and tools to build high quality detection analytics are below:
- Sigma - Sigma main rule repository. The place where detection engineers, threat hunters and all defensive security practitioners collaborate on detection rules. The repository offers more than 3000 detection rules of different type and aims to make reliable detections accessible to all at no cost.
- Microsoft Sentinel Solutions - combinations of data connectors, workbooks, analytic rules, playbooks, hunting queries, parsers, watchlists, and more for Microsoft Sentinel.
- reprise99 Sentinel Queries - Some tips, tricks and examples for using KQL for Microsoft Sentinel.
- Sentinel custom content CI/CD - How to create and manage connections between Microsoft Sentinel and GitHub or Azure DevOps repositories. Managing your content in an external repository allows you to make updates to that content outside of Microsoft Sentinel, and have it automatically deployed to your workspaces.
5.1 Improving Microsoft Sentinel Detection Coverage¶
Under Review
The WA SOC's older detection and automation packs are currently being converted into an external content repository to enable better change management with git.
To improve detection coverage within Microsoft Sentinel, please follow the WA SOC telemetry re-ingestion and incident synchronisation guidance.
6. Sentinel Telemetry Gap Analysis (KQL)¶
The following listed queries help identify missing telemetry for endpoints in Microsoft Sentinel. The chart below depicts most seen observables per MITRE ATT&CK® (source: OSSEM project)
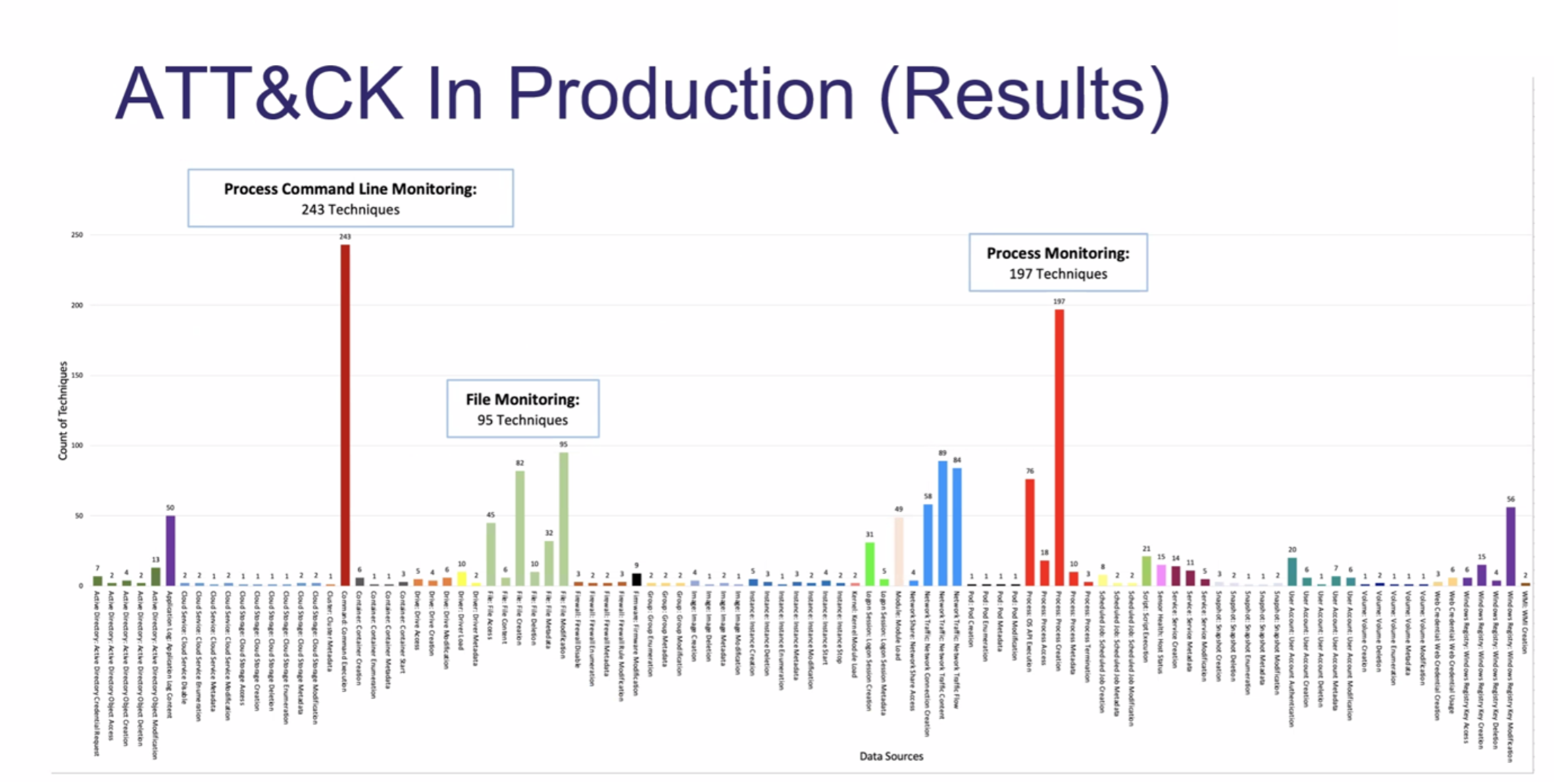
6.1 Process Creation¶
The following are common log sources for Process Creation events and relating kql queries to identify number of endpoints providing these observables.
| Log source | KQL |
|---|---|
| Audit Policy (SecurityEvent) | SecurityEvent | where TimeGenerated > ago(7d) | where EventID == 4688 | summarize count_distinct(Computer) |
| Sysmon (Event) | Event | where TimeGenerated > ago(7d) | where Source == "Microsoft-Windows-Sysmon" | where EventID == 1 | summarize count_distinct(Computer) |
| Defender (DeviceProcessEvents) | DeviceProcessEvents | where TimeGenerated > ago(7d) | summarize count_distinct(DeviceName) |
| AzureAD (VMProcess) | VMProcess | where TimeGenerated > ago(7d) | where isnotempty(ExecutableName) | summarize count_distinct(Computer) |
6.2 Process Command Line¶
The following kql queries will provide number of endpoints with Command Line logging enabled.
| Log type | KQL |
|---|---|
| Audit Policy (SecurityEvent) | SecurityEvent | where TimeGenerated > ago(7d) | where EventID == 4688 | where isnotempty(CommandLine) | summarize count_distinct(Computer) |
| AzureAD: VMProcess | VMProcess | where TimeGenerated > ago(7d) | where isnotempty(CommandLine) |summarize count_distinct(Computer) |
| DeviceProcessEvents | DeviceProcessEvents | where TimeGenerated > ago(7d) | where isnotempty(InitiatingProcessCommandLine) or isnotempty(ProcessCommandLine) | summarize count_distinct(DeviceName) |
6.3 Parent Process¶
| Log type | KQL |
|---|---|
| Audit Policy (SecurityEvent) | SecurityEvent | where TimeGenerated > ago(7d) | where EventID == 4688 | where isnotempty(ParentProcessName) | summarize count_distinct(Computer) |
6.4 Microsoft Defender Device Logs¶
Connect Microsoft 365 Defender to Micrososft Sentinel
Techniques: Microsoft Defender for Endpoint | Microsoft Security¶
| Log type | KQL |
|---|---|
| Process creation and related events | DeviceProcessEvents | where TimeGenerated > ago(7d) | summarize count_distinct(DeviceName) |
| Network connection and related events | DeviceNetworkEvents | where TimeGenerated > ago(7d) | summarize count_distinct(DeviceName) |
| Parent Process | DeviceProcessEvents | where TimeGenerated > ago(7d) | where isnotempty(InitiatingProcessParentFileName) | summarize count_distinct(DeviceName) |
| Named Pipes | DeviceEvents | where ActionType == "NamedPipeEvent" | where TimeGenerated > ago(7d) | summarize count_distinct(DeviceName) |
| File creation, modification, and other file system events | DeviceFileEvents | where TimeGenerated > ago(7d) | summarize count_distinct(DeviceName) |
| Creation and modification of registry entries | DeviceRegistryEvents | where TimeGenerated > ago(7d) | summarize count_distinct(DeviceName) |
| DLL loading events | DeviceImageLoadEvents | where TimeGenerated > ago(7d) | summarize count_distinct(DeviceName) |
6.5 Microsoft Defender Office 365 Logs Monitoring¶
Connect Microsoft 365 Defender to Micrososft Sentinel
| Log type | KQL |
|---|---|
| Email Events | EmailEvents | where TimeGenerated > ago(7d) | summarize Time = max(TimeGenerated) |
| Email Attachment Info | EmailAttachmentInfo | where TimeGenerated > ago(7d) | summarize Time = max(TimeGenerated) |
| Email Url Info | EmailUrlInfo | where TimeGenerated > ago(7d) | summarize Time = max(TimeGenerated) |
| Email Post Delivery Events | EmailPostDeliveryEvents | where TimeGenerated > ago(7d) | summarize Time = max(TimeGenerated) |
6.6 Important activities¶
The table presented below provides a comprehensive list of significant Event IDs that can potentially signify noteworthy activities associated with malicious actions.
| Type | KQL |
|---|---|
| Local Authentication | SecurityEvent | where TimeGenerated > ago(7d) | where EventID == 4624 | summarize count_distinct(Computer) |
| DC Authentication | SecurityEvent | where TimeGenerated > ago(7d) | where EventID == 4776 | summarize count_distinct(Computer) |
| Group Enumeration | SecurityEvent | where TimeGenerated > ago(7d) | where EventID == 4799 | summarize count_distinct(Computer) |
| Kerberos | SecurityEvent | where TimeGenerated > ago(7d) | where EventID == 4769 | summarize count_distinct(Computer) |
| Certificate Usage (Kerb) | SecurityEvent | where TimeGenerated > ago(7d) | where EventID == 4768 | summarize count_distinct(Computer) |
| Replication | SecurityEvent | where TimeGenerated > ago(7d) | where EventID == 4662 | summarize count_distinct(Computer) |
| New Scheduled Task | SecurityEvent | where TimeGenerated > ago(7d) | where EventID == 4698 | summarize count_distinct(Computer) |
| Powershell Execution | SecurityEvent | where TimeGenerated > ago(7d) | where EventID == 4104 | summarize count_distinct(Computer) |
| Registry Value Modification | SecurityEvent | where TimeGenerated > ago(7d) | where EventID == 4657 | summarize count_distinct(Computer) |
| RunAs | SecurityEvent | where TimeGenerated > ago(7d) | where EventID == 4648 | summarize count_distinct(Computer) |
| Windows Firewall Rule Deletion | SecurityEvent | where TimeGenerated > ago(7d) | where EventID == 4948 | summarize count_distinct(Computer) |