DevSecOps Induction¶
1. Getting Started¶
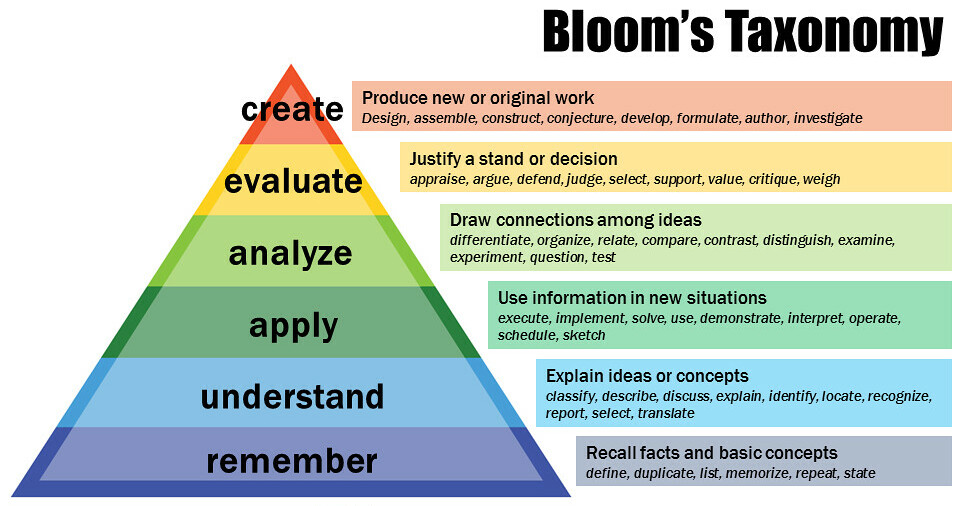
The Learning Journey is an excellent starting point for how to self teach using resources like those below.
By the end of the learning journey course, the learner should be able to:
- Use Obsidian for note-taking and planning
- Recognize the various levels of learning
- Create a Learning Plan and Study Map to guide their journey (also see Maker Skill Trees)
- Effectively evaluate learning/information resources for quality and appropriateness
- Self-assess learning via metacognition
- Create Exhibitions of Mastery to demonstrate success
Note: Timeline estimates assume 5-10 hours of study per week alongside regular work duties. Progress may vary based on prior experience and available study time.
2. Free Training Resources¶
These are our recommended resources for building core technical skillsets.
2.1. Cloud Native Fundamentals (4-6 weeks)¶
👉 New Team Members Start Here!
The below links will get you across the cloud native methodology to build, test and deliver infrastructure and software. These skills apply to the subsequent infrastructure operation and development guidance sections.
- GitLab Basics: Start Using Git: Learn how to set up Git, clone repositories, and work with branches using GitLab. GitLab Basics: Start Using Git
- GitHub Codespaces: Using Source Control: Perform all Git actions directly within your codespace, including committing changes, creating branches, and raising pull requests.
- GitHub Actions: Writing Workflows Quickstart: automate your build, test, and deployment pipeline.
- just is a handy way to save and run project-specific commands. Note that its a cleaner approach to design and implement actions using a tool like
justin your project, and then call the tool from your CI/CD tooling (like GitHub Actions) to make it straightforward to test locally and keep logic portable between CI/CD tools.
- just is a handy way to save and run project-specific commands. Note that its a cleaner approach to design and implement actions using a tool like
- Ansible YAML Syntax: An overview of correct YAML syntax used in Ansible playbooks, including lists, dictionaries, and more.
- Terraform Configuration Syntax: Detailed description of the syntax used in Terraform configuration files, including arguments and blocks.
- Terraform AWS Provider: Use the Amazon Web Services (AWS) provider to interact with the many resources supported by AWS.
- Terraform Azure Provider: The Azure Provider can be used to configure infrastructure in Microsoft Azure using the Azure Resource Manager API's.
-
Kubernetes Basics: A tutorial providing a walkthrough of the basics of Kubernetes workload orchestration.
-
Introduction to Kubectl and Kustomize, especially section on configuration management covering secrets, namespaces, and labels (useful intro vid below).
-
Skaffold handles the workflow for building, pushing and deploying your application, allowing you to focus on writing code.
- Nine Key Cloud Security Concentrations & SWAT Checklist: A set of best practices for cloud security, broken down by AWS, Azure, and GCP, to help create more secure applications.
-
2.2. Cloud Platform Essentials (2-3 weeks)¶
These are intro courses and security overviews of the major AWS and Azure platforms (as they use a lot of cloud specific nomenclature it's worth getting across).
AWS Resources¶
- Amazon EKS Quickstart: Deploy a web app and store data
- AWS Cloud Practitioner Essentials
- AWS Security Fundamentals Second Edition
Azure Resources¶
- Microsoft AKS Quickstart: Deploy an application from a code repository
- Microsoft Azure Fundamentals
- Microsoft Security Academy
2.3. Development Paths¶
Understanding the OWASP Projects focused on Secure Development Life Cycle’s (SDLC) will help in getting across the common security capabilities platforms and software should generally have. The below Data Integration and Frontend Frameworks all are typically secure by default, however the way they are deployed can significantly change their risk profile. For production or high risk environments it’s always best to review the operational procedures against the 2 above standards.
Backend Development (4-6 weeks)¶
Expected outcomes: Basic programming skills, understanding of software design principles and secure development practices
For backends, using a modern API framework like Huma (Your First API tutorial) is strongly recommended. There is a great video series on Golang as well below:
Software and code security¶
- Safestack intro course
- OWASP Application Security Verification Standard for software executing on servers (such as Websites and API’s) - default to ASVS Level 2
- OWASP Mobile ASVS for software executing on clients (such as Mobile Applications) - default to MAS-L2
- Testing & QA - Scan for vulnerabilities and configuration/secret issues with Trivy, Prowler and checkov. Run static analysis of codebases to find common issues with semgrep, CodeQL or Snyq.
- Testing & QA - Test websites with playwright and APIs with Hurl or Grafana K6.
Data Integration (2-3 weeks each)¶
Expected outcomes: Understanding how to ingest/manage data with Python and SQL and generate reports with Markdown
Start with building a web app using evidence.dev (that makes it easy to generate slick Apache ECharts visuals). Once you have the basics of how to collate and view data with SQL, then dive into the SQLMesh CLI quickstart to understand how SQL (and python) can be used to transform data at scale. The large number of execution engines SQLMesh can use in addition to the DuckDB Friendly SQL its in memory processing can do should make almost any data activities easy to model, test and execute.
Massive datasets should use approaches like incremental by time range which enable only loading relevant chunks of data as needed. Using the Athena execution engine across Amazon S3 Tables makes it straightforward to run a managed Apache Iceberg data lake that is suitable for petabyte scale datasets.
Some reporting requirements lead to static / document style reports, in which case Quarto is an excellent open-source scientific and technical publishing system, that supports Hugo markdown for simple documents and Typst for advanced typesetting.
For more details on the languages used by the above tools, see below:
Frontend frameworks (1-2 weeks each)¶
- JavaScript (understand JS basics)
The below frameworks are all focused on having simple, minimal code easy for small teams to maintain.
- Streamlit in browser python prototypes can be used for fast prototypes in python that compiles to browser.
- Hugo and Zola are fast simple static site generators.
- Astro is extensible with Javascript/Typescript.
- Material for MkDocs is extensible with Python/Jinja.
3. Paid Certifications (2-3 months)¶
The SANS courses / certifications are the hardest (at least 50-100hrs study effort per cert) but most in depth:
- SANS SEC540: Cloud Security and DevSecOps Automation - Operations Focus
- SANS SEC522: Application Security: Securing Web Applications, APIs, and Microservices - Development Focus
Otherwise the lower cost certs below are all a fair bit shorter while also being high quality:
- Linux Foundation Certified Kubernetes Administrator (CKA) + Certified Kubernetes Application Developer (CKAD) + Certified Kubernetes Security Specialist (CKS) Exam Bundle
- AWS Certified Solutions Architect - Associate
- Microsoft Certified: Azure Developer Associate
4. Useful links and tools¶
- Maker Skill Trees are printable templates that can you can use to visualize your skill progress, identify skill gaps and get inspired to try new things.
- excalidraw: Virtual whiteboard for sketching hand-drawn like diagrams, can import/edit mermaid diagrams.
- Talos Linux is Linux designed for Kubernetes – secure, immutable, and minimal. It only takes 3 minutes to launch a Talos cluster on your laptop inside Docker.
- Percona Everest: open-source platform for automated database provisioning and management. It supports multiple database technologies and can be hosted on any Kubernetes infrastructure, in the cloud or on-premises.
- LocalStack is a cloud service emulator that runs in a single container on your laptop or in your CI environment.
- project Bluefin: Linux workstation, designed for reliability, performance, and sustainability.
- Homebrew: The Missing Package Manager for macOS (or Linux)
- just is a handy way to save and run project-specific commands.
- DGOV DTT Architecture Decision Records is a list of architecture decisions supporting DTT platforms and capabilities.
- ugrep is a more powerful, ultra fast, user-friendly, compatible grep replacement. Includes a TUI, Google-like Boolean search with AND/OR/NOT, fuzzy search, hexdumps, searches (nested) archives (zip, 7z, tar, pax, cpio), compressed files (gz, Z, bz2, lzma, xz, lz4, zstd, brotli), pdfs, docs, and more.
- Page Assist is an open-source browser extension that provides a sidebar and web UI for your local AI model.
- ollama can run Llama 3.3, DeepSeek-R1, Phi-4, Mistral, Gemma 2, and other models, locally.
4.1 Certified Kubernetes platforms¶
The below hyperscaler managed Certified Kubernetes platforms all automate the operations of compute nodes, block storage and network load balancers which greatly simplifies running k8s workloads.