SOC Analyst Induction¶
1. Overview¶
The below guidance is to get a novice with basic IT literacy up to speed with common Security Operations activities all the way from collecting events, alerting on detections, triaging alerts, responding to incidents and managing detection rules and investigative queries.
The Learning Journey (The Taggart Institute) is an excellent starting point for how to self teach using resources like those below.
2. Prerequisites¶
To get started with SOC activities in the Microsoft Sentinel environment it is sensible to have administrative access to both a Microsoft 365 tenant and a Microsoft Azure subscription.
There are developer/student versions available for free that should be sufficient for the training exercises below:
- Microsoft 365 Developer Program - Free for anyone with a mobile number, no credit card required.
- Azure for Students - Free for anyone with an edu email address, no credit card required.
- Azure free account - Free for anyone with a credit card verification step, no ongoing payment required.
- JupyterLab Desktop - Free desktop tool for python notebooks to complete security research and investigations.
Please use the above links or existing services to organise yourself admin access, then work through the training below.
3. Recommended structured learning approach¶
The below training provides a good foundational base for cyber security defensive activities. It's recommended to work through them in order.
3.1. IT Infrastructure and Cloud fundamentals¶
Most IT services are delivered as layers ontop of several supporting services.
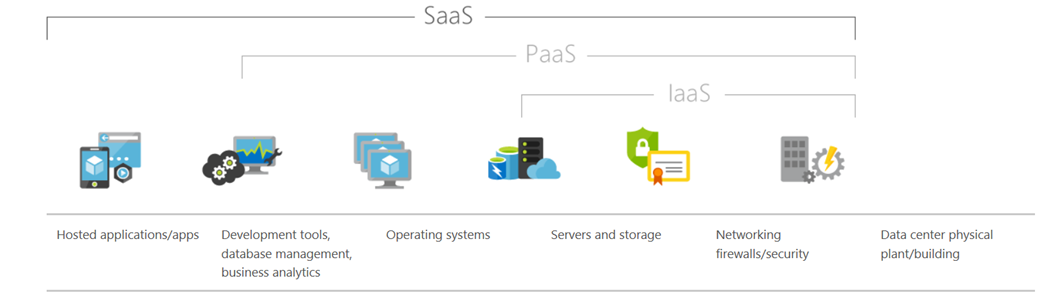
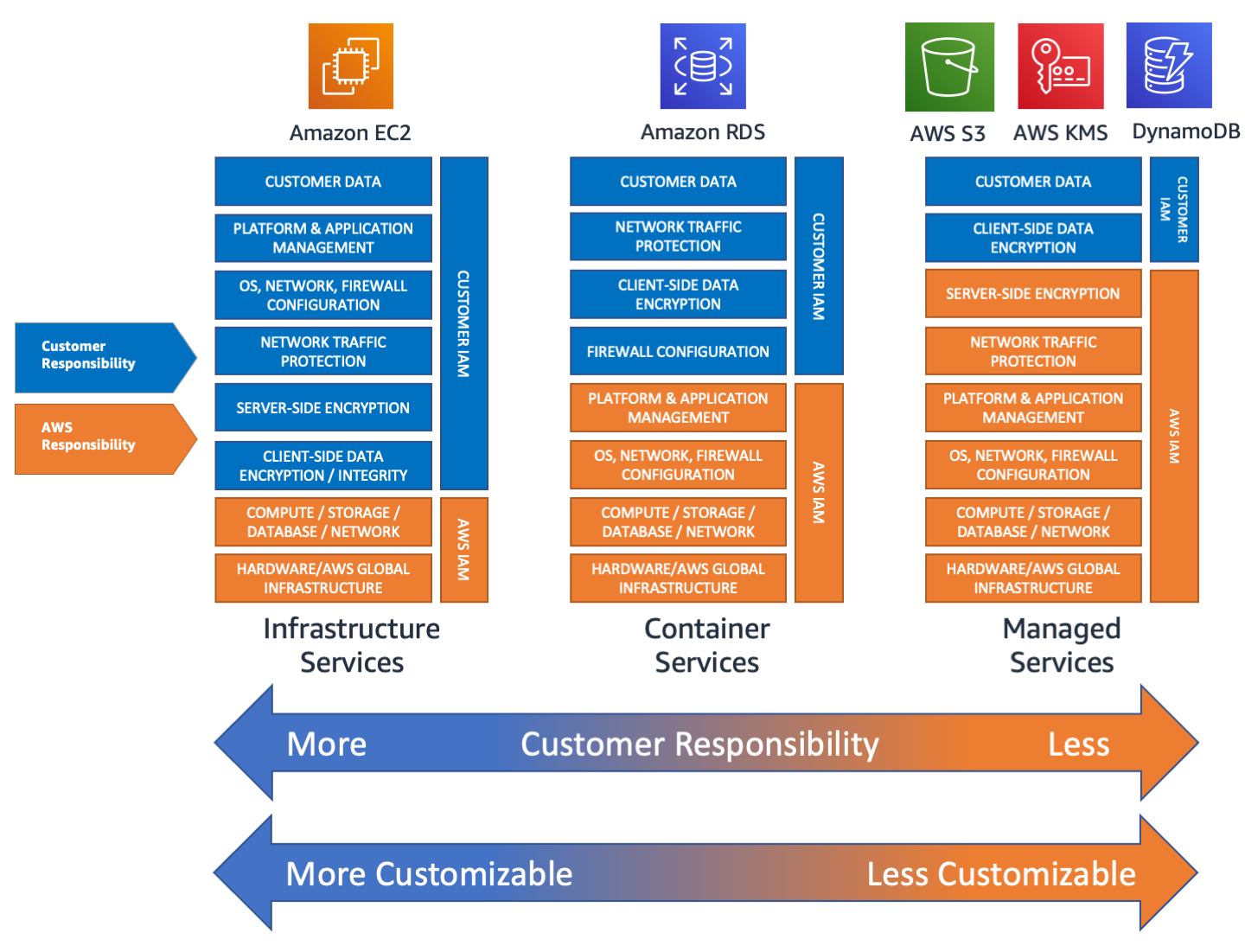
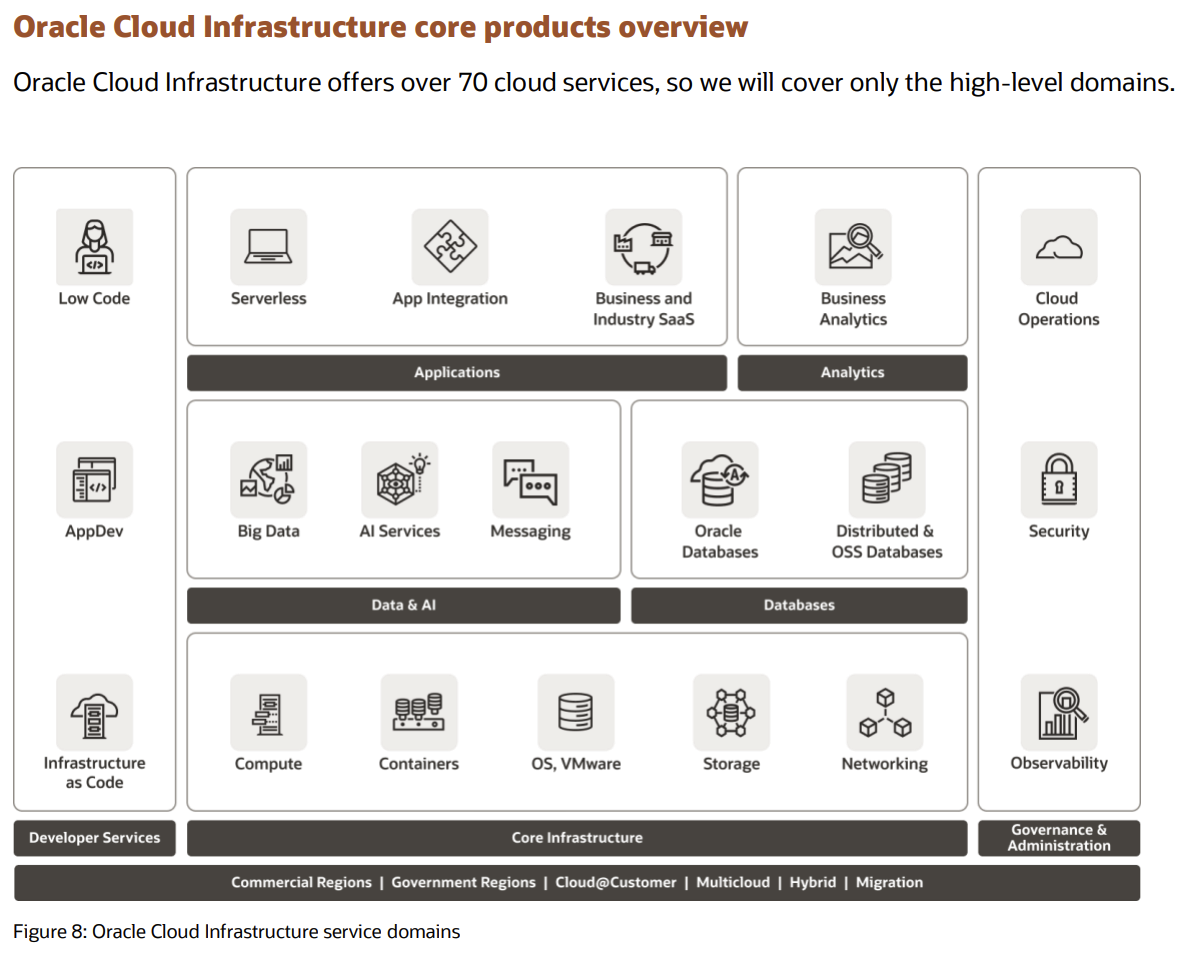
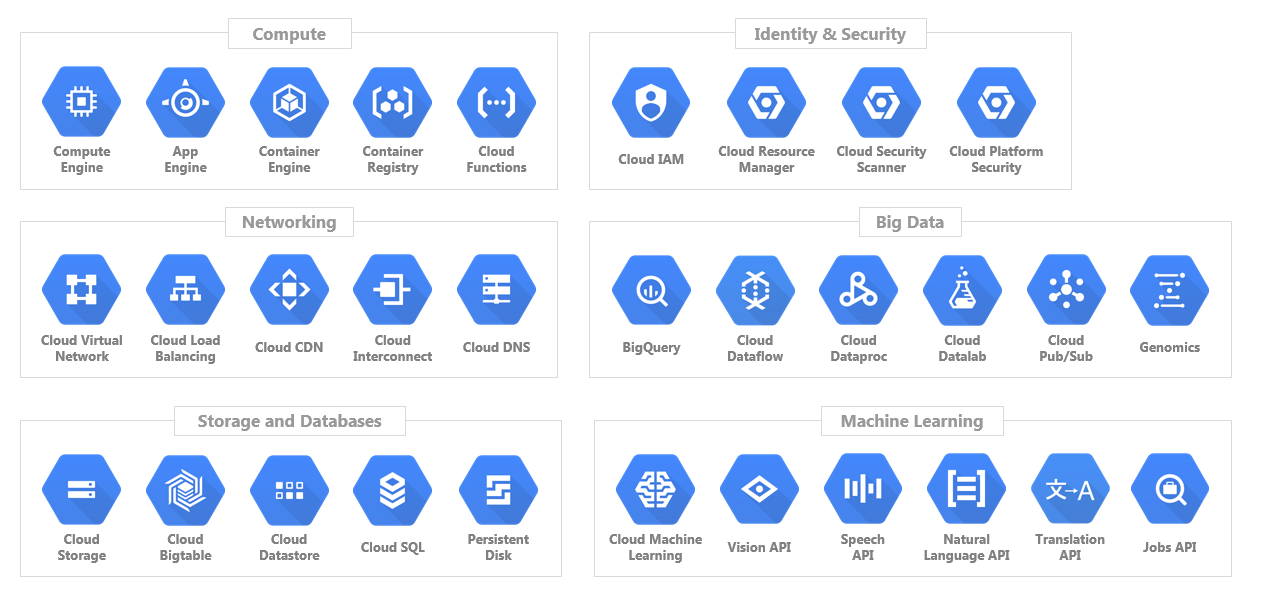
To secure a modern public cloud start with understanding shared security responsibility models. It is crucial to understand where to effectively apply investment (i.e. where to focus security resources) to ensure a useful outcome.
If you are relatively new to public cloud services and/or IT infrastructure, please start with the Azure Fundamentals (AZ-900) and Security, Compliance, and Identity Fundamentals (SC-900) certifications.
3.2. Security Operations Basics¶
Learn the basics of triaging and responding to incidents, including collaboration with organisational stakeholders.
- Microsoft Security Operations Analyst (SC-200) Certification
- Microsoft 365 Certified: Enterprise Administrator Expert (MS-102) Certificate
- TryHackMe MITRE Training (Optional: Cybrary MITRE ATT&CK Defender (MAD))
3.2.1. Documentation, Programming and scripting fundamentals¶
Learn how to create documentation in markdown, keep track of your work in git, code in python and automate tasks in powershell. Developing good documentation skills, and having a good grasp of coding and scripting significantly enhances your abilities to compose information and orchestrate computers, both excellent skills to have in your toolbelt as a security professional.
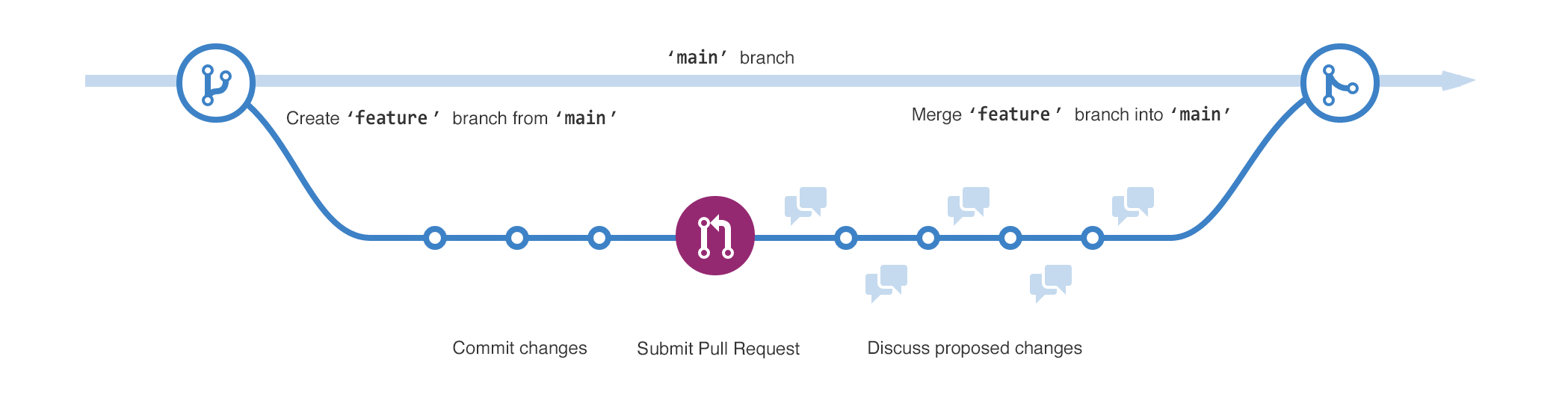
- Basic writing and formatting guide (GitHub Markdown) - use markdown docs in git repos for managing code, detection rules, investigation evidence.
- Also see Oh My Git! - use git to manage all your work and track who has changed what.
- Python for defenders from taggart-tech.com is also a very good resource, focused on using Python from a blue team perspective.
- Also see Automate administrative tasks by using PowerShell - learn to run commands, how to learn more about PowerShell and it's modules and additionally to create and run script files.
- How to ask Technical Questions (Princeton) - once you are dealing with complex technical activities, having a good approach for understanding where to look next for assistance is a very useful skill.
3.2.2. Creating and securing public cloud workloads¶
Please work through the Azure VM excercises to familiarise yourself with the tools that would typically be used to build and run a secure cloud workload as a VM exposed to the internet.
3.2.3. Security Investigations with Python Notebooks¶
Connect to SIEM tools from python notebooks (also known as Jupyter Notebooks), and use pandas to interrogate, analyse and report on datasets at scale. Keeping track of advanced investigative activities in python notebooks is a good way to share complex procedures in an open, repeatable, refinable format that can be rapidly re-used for subsequent investigations.
Once you have a handle on developing the above notebooks, you should be able to export some data from your tools and rapidly assess it using community threat intelligence resources such as:
- urlscan.io - Website scanner for suspicious and malicious URLs.
- VirusTotal - Analyze suspicious files, domains, IPs and URLs to detect malware and other breaches, automatically share them with the security community.
- AbuseIPDB - central repository of IP abuse reports.
- Shodan - details of internet connected devices updated weekly.
3.3. Skill Check - Develop a Security Notebook¶
Develop a security notebook that reads security event data from a local csv and check the entities/indicators/observables against a community api such as urlscan.io or VirusTotal to validate if there is any known sources of concern.
- Develop your security investigative notebooks in a git repository to share with your team.
- Test with known malicious indicators to validate they work.
- Include usage documentation for your notebook in markdown in your git repository.
3.4. Cheatsheets¶
The below one pagers are great to print out and use as reference material while familiarising yourself with tools.
- Regular Expressions - regex including symbols, ranges, grouping, assertions and some sample patterns to get you started.
- Kusto Query Language (KQL) - queries mainly focused on the SecurityEvent table.
- Python - one-page reference sheet for the Python programming language.
- Pandas - Data Wrangling with pandas Cheat Sheet.
3.5. Microsoft tooling in depth¶
For those using a Microsoft toolset the below guides have in-depth details on operating a SIEM, managing security across microsoft tools, and securely operating systems on Microsoft Azure. The WA SOC maintains the WA SOC Microsoft Sentinel Connector Guidance intended to be a guided path to achieving good security coverage using primarily Microsoft Sentinel as a SIEM.
3.5.1. Understanding Kusto Query Language (KQL)¶
The below two resources are a good starting point for understanding KQL in addition to the Microsoft KQL Overview.
- KQL Overview Overview video of the whole language (1 hour).
- Must Learn KQL A blog/book/video channel.
- Kusto Detective Agency Use KQL as an investigation tool as part of a virtual agency with cases.
3.5.2 Addtional Microsoft Security and Administration Training¶
The below resources are addtional training material for better understading the Microsoft Sentinel and M365 Security tools. Microsoft has developed the Microsoft Security Academy, the following are high priority for SOC Analysts:
- Become a Microsoft Sentinel Ninja: The complete level 400 Training
- Become a Microsoft Unified SOC Platform Ninja Training
- Become a Microsoft 365 Defender Ninja Training
- Become a Microsoft 365 Defender Ninja Training
- Cybersecurity Architect Expert (SC-100) Certification - design forward-looking strategies for security, governance, risk, compliance covering users, workstations, infrastructure, data and applications.
- Microsoft Certified: Identity and Access Administrator Associate (SC-300) Certification - configure and manage authentication and authorization of identities for users, devices, Azure resources, and applications.
- Microsoft Certified: Information Protection Administrator Associate (SC-400) Certification - implementing and managing solutions for content classification, data loss prevention (DLP), information protection, data lifecycle management, records management, privacy, risk, and compliance.
3.6. Public cloud tooling in depth¶
Several other cloud providers have operational security training that is designed for easy adoption on their platforms, relevant certifications of interest are below (note there is high overlap between cloud providers, so the microsoft training above should make the below learning paths much easier to complete).