Cyber Security Playbooks¶
Over time the WA SOC is establishing a set of playbooks, primarily focused on incident response that are suitable for cyber security teams with operational processes aligned to the CISA Cybersecurity Incident and Vulnerability Response Playbooks (508C) and the MITRE 11 Strategies of a World-Class Cybersecurity Operations Center.
1. Triage & Investigation¶
Under Review, see Sentinel Triage AssistanT (STAT) as an approach to standardise and automate common triage actions.
2. Incident Response¶
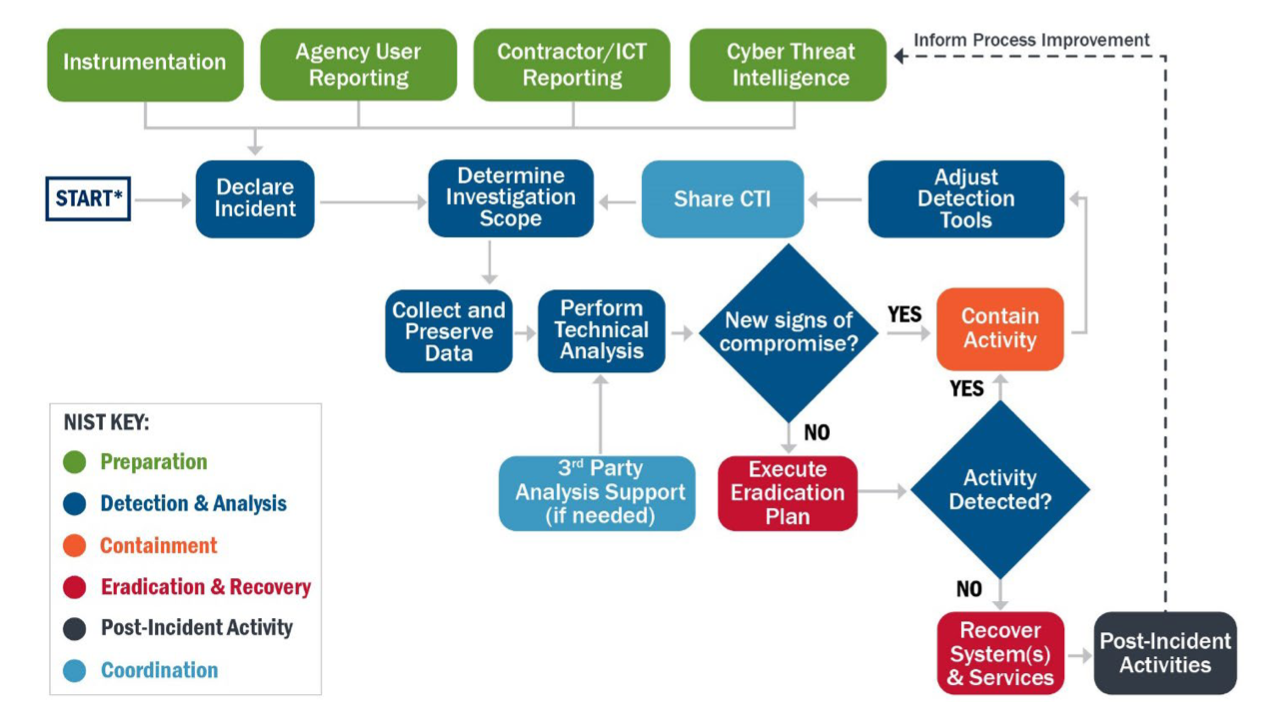
In the absence of an internal procedure the CERT Societe Generale IRM-2022 (Incident Response Methodologies 2022) are a good starting point covering the below common scenarios:
- Worm Infection (pdf)
- Windows Intrusion (pdf)
- Unix, Linux Intrusion Detection (pdf)
- Distributed Denial Of Service - DDOS (pdf)
- Malicious Network Behaviour (pdf)
- Website Defacement (pdf)
- Windows Malware Detection (pdf)
- Blackmail (pdf)
- Smartphone Malware (pdf)
- Social Engineering (pdf)
- Information Leakage (pdf)
- Insider Abuse (pdf)
- Customer Phishing (pdf)
- Scam (pdf)
- Trademark infringement (pdf)
- Phishing (pdf)
- Ransomware (pdf)
- Large scale compromise (pdf)
- Third-Party Compromise (pdf)
- Red Team Detection (pdf)
- Critical Vulnerability Prioritisation (pdf)
- Business Email Compromise (pdf)
3. Vulnerability Response¶
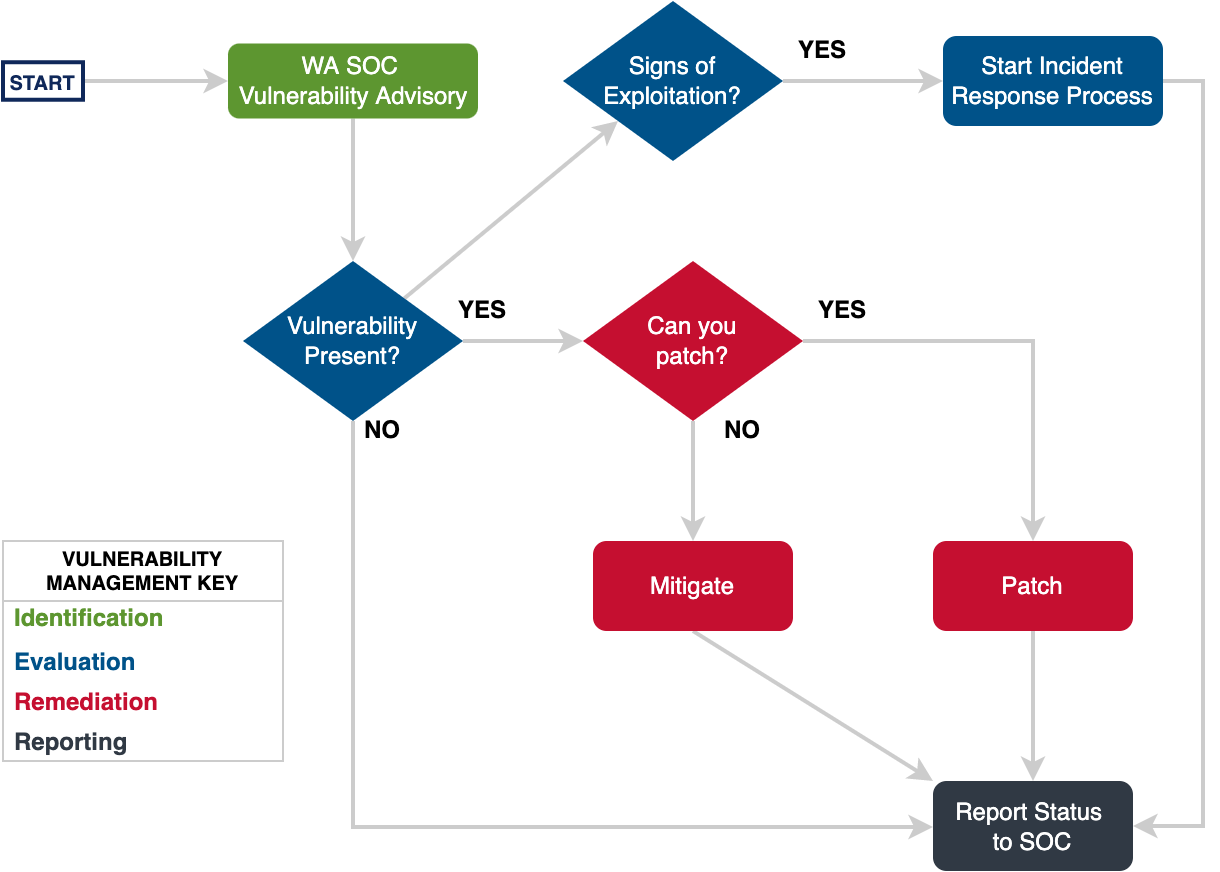
Under Review, refer to Technical Example: Patch Operating Systems and Technical Example: Patch Applications for good approaches to automating baseline vulnerability management.
4. Threat Hunting¶
Under Review, Jupyter Notebooks are effective, and easily query datalake type repositories, see Use a Jupyter Notebook and kqlmagic extension to analyze data in Azure Data Explorer.
5. Digital Forensics¶
Under Review, see Collecting Evidence and Dissect (modern forensics tooling) to augment SIEM activities with in depth captures as needed.